The research at SPIES group is regularly featured in prominent national and international media venues (selected recent examples below). For any media inquiries and interview requests, please contact Prof. Nitesh Saxena.
Cognitive Security
- Saxena and team awarded $6M DOD grant on cognitive security, Texas A&M Engineering Experiment Station, May 3, 2023
- We Can’t Tell the Difference Between a Robot and Human Voice, Daily Beast, April 25, 2019
- Lend me your ears and AI will play with your brain: Machine voice imitators outsmart us, The Register, April 4, 2019
- The crux of voice (in)security: a brain study of speaker legitimacy detection, The morning paper, April 1, 2019
- Are human brains vulnerable to voice morphing attacks?, UAB News, March 8, 2019
- UAB research studies cyberattacks through the lens of EEG and eye tracking, UAB News, Oct 22, 2015
- Research studies cyberattacks through the lens of EEG and eye tracking, Phys.org, Oct 23, 2015
- Cyberattacks studied through the lens of EEG and eye tracking, Science News, Oct 23, 2015
- UAB Research Studies Cyberattacks Through the Lens of EEG and Eye Tracking, Newswise, Oct 23, 2015
- Research Studies Cyberattacks Through The Lens Of EEG And Eye Tracking, ECN, Oct 23, 2015
- Research studies cyberattacks through the lens of EEG and eye tracking, Geek Journal, Oct 23, 2015
- Research studies cyberattacks through the lens of EEG and eye tracking, Follow News Oct 23, 2015
- Cyberattacks studied through the lens of EEG and eye tracking, My Clever Mind Oct 23, 2015
- UAB research studies cyberattacks through the lens of EEG and eye tracking, Wn.com Oct 23, 2015
- Research studies cyberattacks through the lens of EEG and eye tracking, Three Novices Oct 23, 2015
- Research Studies Cyberattacks Through the Lens of EEG and Eye Tracking, Make Me Feed, Oct 23, 2015
- Cyber Attacks Studied Through Lens of EEG and Eye Tracking, News United, Oct 24, 2015
- Cyberattacks studied through the lens of EEG and eye tracking, IT Security News Oct 24, 2015
- Better understanding of how computer users detect malware and phishing attacks, Homeland Security News Wire, Oct 27, 2015
- Studying Cyberattacks through Lens of EEG and Eye Tracking, Scientific Computing, Oct 27, 2015
- Users fail to identify phishing attacks, study says, Network World, Oct 29, 2015
- UAB Research Studies Cyberattacks Through the Lens of EEG and Eye Tracking, Communications of the ACM, Oct 26, 2015
- Detection of cyber attacks through the lens EEG and eye tracking, Mirin, Nov 2, 2015
- Cyberattacks studied through the lens of EEG and eye tracking, USN World Nov 3, 2015
- How your Brain is affected by Phishing Scams, BlogHer, Feb 10, 2015
- Los internautas temen a los hackers menos de lo que dicen, La Razon, Nov 30, 2014
- Our brains work hard to spot phishing scams, but still often fail, NakedSecurity, March 4, 2014
- Most People Can’t Tell the Difference Between a Real Website and a Scam, Motherboard, March 5, 2014
- Users’ brains scanned in bid to fix infosec, CSO, March 15, 2014
- Nehezen különböztetjük meg a valódi és az adathalász honlapoka (Hungarian), S.hu, March 10, 2014

- Neue Studie zu Phishing: Opfer kennen die Warnsignale nicht (German), Gulli, March 6, 2014
- Brain research tracks internet safety performance, dispels assumptions, identifies traits of those at-risk, Science Daily, February 28, 2014
- Study suggests users pay more attention to Internet safety than previously assumed, Phys.org, February 28, 2014
- Brain research tracks Internet safety performance, dispels assumptions, identifies traits of those at-risk, UAB News, Feb 27, 2014
Opted Out, Yet Tracked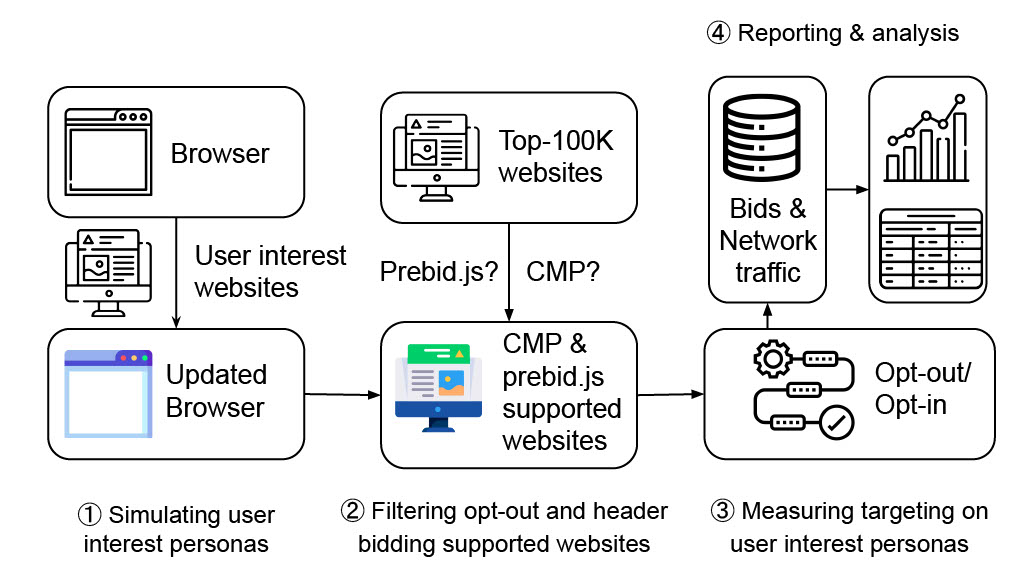
- Even After Opting Out, Your Data May Still Be Shared, GMA, March 10, 2023
- Tech-Insight : Even After Opting Out, Your Data May Still Be Shared, BEESO IT, March 8, 2023
- Tech-Insight : Even After Opting Out, Your Data May Still Be Shared, Surf Tech IT, March 8, 2023
- Research: Refusing online tracking has little effect, DIVBRACKET, March 3, 2023
- Enquête: refuser le traçage en ligne n’a guère d’utilité, KNOWLEDIA, March 4, 2023
- Thought you’d opted out of online tracking? Think again, The Register, March 3, 2023
- Opt-out geeft consument géén opt-out, blijkt uit onderzoek, AG Connect, March 6, 2023
- Enquête: refuser le traçage en ligne n’a guère d’utilité, DataNews, March 3, 2023
- Onderzoek: Weigeren van online tracking haalt soms maar weinig uit, Dutch IT Channel, March 6, 2023
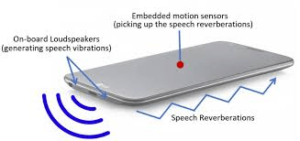
EarSpy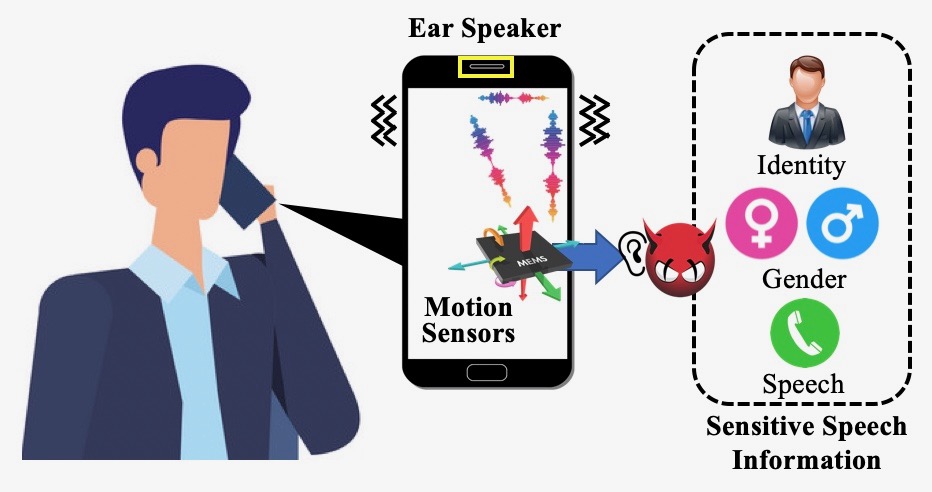
- Researchers Hack Android Smartphones, Find A Security Risk, Texas A&M Today, August 28, 2023
- Research reveals call security risk in smartphones, Tec Rounder, August 23, 2023
- Research Hack Reveals Call Security Risk in Smartphones, Communications of the ACM, August 23, 2023
- Research hack reveals call security risk in smartphones, Texas A&M Engineering, August 17, 2023
- Research hack reveals call security risk in smartphones, Tech Xplore, August 22, 2023
- Research hack reveals call security risk in smartphones, News8Plus , August 22, 2023
- Research hack reveals call security vulnerability in smartphones, Crash.net, August 22, 2023
- This creepy Android flaw can detect your identity and even gender, MSN, December 28, 2022
- EarSpy — A New Attack on Android Devices Use Motion Sensors to Steal Sensitive Data, Medium.com, January 7, 2023
- EarSpy can eavesdrop on your phone conversations using motion sensors, Android Police, January 1, 2023
- How hackers could use popular virtual reality headsets to steal sensitive informatioEarSpy : cette technique permet d’écouter vos appels grâce à l’accéléromètre, CNET France, January 3, 2023
- EarSpy Attack Can Use Motion Sensors Data to Pry on Android Devices, Hackread, December 29, 2022
- EarSpy attack eavesdrops on Android phones via motion, Bleepingcomputer, December 27, 2022
- EarSpy: Spying on Phone Calls via Ear Speaker Vibrations Captured by Accelerometer, Securityweek, December 28, 2022
- EarSpy Spying on Phone Calls via Ear Speaker Vibrations Captured by Accelerometer, Odaloop, 2 January 2023
- EarSpy can spy on your phone calls by using motion sensors, Android Headlines, 2 January 2023
- EarSpy can eavesdrop on your phone conversations using motion sensors, Reddit, 2 January 2023
- Android: Interception of calls through.. motion sensors!, iTechnews Greece, January 5, 2023
- Can the New EarSpy Hack Eavesdrop on Your Phone Conversations Through Vibrations?, Timesnow News India, January 3, 2023
- EarSpy, Android and how smartphones can be eavesdropped, Lifestyle.bg Bulgeria, January 3, 2023
- EarSpy’s research has proven that Androids can be eavesdropped by vibrations picked up by the accelerometer, MobileMania Czech Republic, December 29, 2022
- EarSpy – A New Attack on Android Devices Use Motion Sensors to Steal Sensitive Data, GBhackers on Security, December 30, 2030
- Security: how your smartphone’s call speaker can be used without your knowledge, Frandroid France, January 2, 2023
Predatory Medicine
- Predatory Medicine: Exploring and Measuring the Vulnerability of Medical AI to Predatory Science, Montreal AI Ethics Institute, October, 22 2022
Security Improvements of 2FA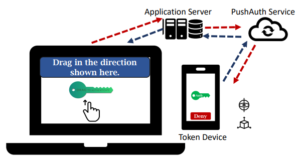
- New Methods Could Improve Security Of Two-Factor Authentication Systems, Texas A&M Today, Aprill, 15 2022
Kids-related Password and Security
- New York Times kids interview, Twitter, Aprill, 28 2022
Face-Mic: AR/VR Speech Eavesdropping
- Unexpected Security Vulnerability Discovered in Gaming Devices, iHLS, Feb, 13 2022
- The main safety problems in virtual reality headsets, according to researchers, Tech Smart, Feb 11, 2022
- Security Vulnerabilities Found in VR Headsets, My Tech Decisions, Feb 14, 2022
- How hackers could use popular virtual reality headsets to steal sensitive information, Help Net Security, Feb 18, 2022
- Your VR headset is likely vulnerable to this new eavesdropping attack, Tweak Town, Feb 22, 2022
Nation State Attacks and Authentication
- Texas Congressman Tony Gonzales calls for cyber actions against Russia, Monica Madden, Jan 26, 2022
Gummy Browsers
- Gummy Browsers Attack: The Latest Cyber Threat in Town, Website Security Store, November 9, 2021
- Gummy Browsers Attack Lets Hackers Spoof Browser’s Digital Fingerprints, Cysecurity News, October 26, 2021
- New Attack Let Attacker Collect and Spoof Browser’s Digital Fingerprints, The Hacker News, October 25, 2021
- New Attack ‘Clones’ and Abuses Your Unique Online ID via Browser Fingerprinting, UNITE.AI, October 20, 2021
- New Gummy Browsers attack lets hackers spoof tracking profiles. Bleeping Computer, October 20, 2021
- Gummy Browsers: The New Cyberattack Developed by Researchers, Heimdal Security, October 21, 2021
Speech Privacy Exploit via Accelerometer of Smartphones
- New Attack Lets Android Apps Capture Loudspeaker Data Without Any Permission, The Hacker News, July 2019
- Android phone’s accelerometer can eavesdrop on any audio via its speakerphone, SC Media, July 2019
- Popular Samsung, LG Android Phones Open to ‘Spearphone’ Eavesdropping, Threat Post, July 2019
- Your Android’s accelerometer could be used to eavesdrop on your calls, Naked Security, July 2019
- Spearphone Attack Allows Android Apps to Listen To Your Loudspeaker Conversations, Latest Hacking News, July 2019
- Spearphone, Security Boulevard, July 2019
- Latest Attack on Android Known as “Spearphone Attack”, Cyberops, July 2019
- Spearphone A Attack for Andriod Phones, Channel Pro Network, July 2019
- Spearphone Assault Permits Android Apps Hear To Telephone Loudspeaker, ETHHack, July 2019
- Popular Samsung, LG Android Phones Open to ‘Spearphone’ Eavesdropping, OODALOOP, July 2019
- Snap! Spearphone eavesdropping, Spiceworks, July 2019
- Abusing Android Accelerometer to Capture Loudspeaker Data, Debug Lies News, July 2019
- New Attack Lets Android Apps Capture Loudspeaker Data Without Any Permission, Linux Security, July 2019
- Android Apps Capture Loudspeaker Data Without Any Permission, BGD e-GOV CIRT, July 2019
- Popular Samsung, LG Android Phones Open to ‘Spearphone’ Eavesdropping, IGRC, July 2019
- Privacy At Risk! Android Apps Capturing Loud Speaker Data Without Permission, InfoSec Intelligence, July 2019
- Spearphone Attack Allows Android Apps to Listen To Your Loudspeaker Conversations, Quantus SEC, July 2019
Listening-Watch: Wearable Two-Factor Authentication
- Developers from Birmingham created a voice-based 2FA system, Tproger, Aug. 25, 2018
- More Security, Less Effort — Researchers Propose Two-Factor Authentication Using Smartwatch Microphone, Forensic Magazine, Sept. 7, 2018
- Researchers propose new method for secure, speech-based two-factor authentication, IT Security News, Aug 26, 2018
- Researchers propose new method for secure, speech-based two-factor authentication, HITBSecNews, Aug 26, 2018
- Listening-Watch wearable system provides secure 2FA, CSO from IDG, Aug. 27, 2018
- Speech-Based Two-Factor Authentication Thwarts Digital Crime, ECN, Aug 24, 2018
- Listening Watch sounds out security idea with websites that listen, Naked Security, Aug 29, 2018
- Researchers pitch voice recognition as two-factor authentication method for wearables, BIOMETRIC UPDATE.COM, Aug. 27, 2018
- Researchers propose new method for secure, speech-based two-factor authentication, TechXplore, Aug. 24, 2018
- Listening-Watch: Strong, low-effort, wearable 2FA scheme, HELPNET SECURITY, Aug. 27, 2018
- Researchers Propose New Method for Secure, Speech-Based Two-Factor Authentication, newswise, Aug. 24, 2018
- New two-factor authentication approach, SD Times, Aug. 27, 2018
- Experimental Authentication System Uses Speech Recognition and a Smartwatch, FINDBIOMETRICS, Aug. 30, 2018
- Researchers propose new method for secure, speech-based two-factor authentication, UAB News, Aug. 23, 2018
Password Manager
- The Best Password Managers, According to Security Experts, The Strategist, August 27, 2021
- What are SPHINX and DE-PAKE?, Devolutions,
VibWrite: Finger Vibrations to Authenticate Users
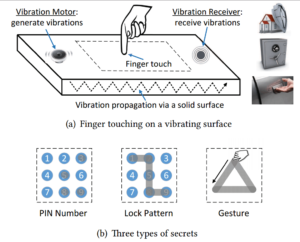
Illustration of a finger touching on a solid surface under physical vibration, and three independent types of secrets for pervasive user authentication.
- VibWrite Finger-Vibration System Turns Doors Into Touchpads, IEEE SPECTRUM, November 2, 2017
- New VibWrite System Uses Finger Vibrations To Authenticate Users, Slashdot, October 31, 2017
- Tapping into a new security trend, Yahoo Finance, October 30, 2017
- Good vibrations: smart access to homes and cars using fingers, NSF Science 360 News, 2017
- Good Vibrations: Smart Access to Homes and Cars Using Fingers, Rutgers Today, October 29, 2017
- Good Vibrations: Smart Access to Homes and Cars Using Fingers, Science Newsline Technology, October 30, 2017
- Smart Access for Homes and Cars Using Fingers Developed, Electronics 360, October 30, 2017
- Good vibration: Smart access to homes and cars using fingers, HiTechDays.com, October 30, 2017
- VibWrite: Smart Access to Homes and Cars using Fingers, Tech Explorist, October 30, 2017
- Good vibration: Smart access to homes and cars using fingers, Herb Approach, October 29, 2017
- Tapping into a new security trend with the touch of a finger, 24News.ca, October 30 , 2017
- New VibWrite System Uses Finger Vibrations to Authenticate Users, BleepingComputer, October 31, 2017
- Here comes a finger vibration-based system to secure your car, The Economic Times, October 30, 2017
- VibWrite can transform any surface into a secure biometric ID sensor, Digital Trends, November 3, 2017
- Rutgers enigneers develop finger vibratio-based access system, Biometric Update.com, October 31, 2017
- Good vibrations: smart access to homes and cars using fingers, FMSM News, November 1, 2017
- Good vibrations: Smart access to homes and cars using fingers, NEW ZEB, October 30, 2017
- Good vibrations: Smart access to homes and cars using fingers, Science Daily, October 30, 2017
Passively Eavesdropping Passwords and Medical Information via Brainwave Signal
- Brainwave devices can leak sensitive medical conditions and personal information, TechXplore, Dec. 19, 2019
- Hackers Could Soon Be Using Brain Waves To Steal Passwords, FILEHIPPO, Jul. 13, 2018
- Using Brainwaves to Guess Passwords, MIT Technology Review, May 5, 2017
- Hackers could soon tap into your brainwaves to guess your passwords, IBT Times, May 9, 2017
- Hackers can use BRAINWAVES fed into gaming headsets to guess passwords and other private information, Daily Mail, May 8, 2017
- Brainwave-Reading Headsets Could Help Hackers Guess Your Password, Popular Mechanics, May 5, 2017
- How Your Brainwaves Can Be Used To Steal Passwords And Private Data, Fossbytes, May 6, 2017
- How hackers can hijack brainwaves to capture your passwords, ZDNet, May 8, 2017
- Tu cerebro revelará contraseñas a los hackers, Media-Tics, May 16, 2017
- Les pirates pourraient-ils détourner vos ondes cérébrales pour subtiliser vos mots de passe Une experience suggere que cela n est pas improbable, Developpez.com, May 8, 2017
- Piratear el cerebro para robar contraseñas, Influencers (Comunicado de prensa) (blog), May 12, 2017
- Los pensamientos también pueden ser pirateados, tendencias21 May 14, 2017
- Estudio revela cómo se pueden descifrar contraseñas analizando ondas cerebrales, Por Jhoanell Angulo, May 9, 2017
- Onde cerebrali, la nuova frontiera dell’hackeraggio, Linkiesta, May 17, 2017
- Hoe hackers wachtwoorden kunnen stelen via hersengolven, DataNews, May 8, 2017
- Hackers could soon tap into your brainwaves to guess your passwords, secnews24, May 9, 2017
- Hackers could soon tap into your brainwaves to guess your passwords, Europe Breaking News, May 9, 2017
- Beware! Hackers could use your brainwaves to guess your password, Ripples Nigeria, May 9, 2017
- Malicious Software: University Study Unveils How Headsets Can Use Brainwaves To Steal Passwords, University Herald, May 6, 2017
- A simple neyrointerfeys for “reading” of passwords in mind , Rusbase, May 5, 2017
Side Channel Attack and Defense
- Researchers Investigate Potential Threat to Speech Privacy via Smartphone Motion Sensors, ACM TechNews, Communications of the ACM, June 18, 2018
- Potential threat to speech privacy via smartphone motion sensors, Homeland Security News Wire, June 18, 2018
- Researchers investigate potential threat to speech privacy via smartphone motion sensors, TechXplore, June 15, 2018
- Are Smartphone Motion Sensors A Security Risk?, ECNMag, June 15, 2018
- Researchers investigate potential threat to speech privacy via smartphone motion sensors, UAB News, June 14, 2018
- Research proposes background noise to prevent side channel attacks on computer keyboards, TechXplore, Sep 27, 2016
- Research proposes background noise to prevent side channel attacks on computer keyboards, UAB News, Sep 26, 2016
- Research proposes background noise to prevent side channel attacks on computer keyboards, WN.com, Sep 26, 2016
- Research proposes background noise to prevent side channel attacks on computer keyboards, Voat, Sep 27, 2016
- The next cyberattack could come from sound waves, The Conversation, March 27, 2017
- The next cyberattack could come from sound waves, Yahoo! Tech, March 27, 2017
- Sound waves being used to launch cyber attacks!, Cybersecurity Insiders, March 27, 2017
- Commentary: The next cyberattack could come from sound waves, CHANNEL NEWSASIA, March 29, 2017
- The next cyberattack could render your anti-virus and encryption software useless, Business Insider, March 27, 2017
Defense against Smartphone Keyloggers
- Research finds novel defense against sophisticated smartphone keyloggers, UAB News, Sept 02, 2016
- UAB researchers find way around malicious attacks on Android devices, Birmingham Business Journal, Sept 08, 2016
- UAB researchers find way around malicious attacks on Android devices, Tuscaloosa News.Net, Sept 09, 2016
- Research finds novel defense against sophisticated smartphone keyloggers , Wn.com, Sept 02, 2016
- Research Finds Novel Defense Against Sophisticated Smartphone Keyloggers, Public., Sept 02, 2016
- Research finds novel defense against sophisticated smartphone keyloggers, TechXplore, Sept 05, 2016
Zero-Effort Security
- Is zero-effort computer security a dream? Breaking a new user verification system, UAB News, Feb 24, 2016
- Is zero-effort computer security a dream? Breaking a new user verification system, Science Daily, Feb 24, 2016
- Is Zero-Effort Computer Security a Dream? Breaking a New User Verification System, Newswise, Feb 24, 2016
- Is zero-effort computer security a dream? Breaking a new user verification system, Tech Xplore, Feb 25, 2016

- Is Zero-effort Computer Security a Dream? Breaking a New User Verification System, Scientific Computing, Feb 25, 2016
- Is zero-effort computer security a dream? Breaking a new user verification system, Sci24H.com, Feb 25, 2016
- Is zero-effort computer security a dream?, Help Net Security, Feb 26, 2016
- Is zero-effort computer security a dream?, IT Security News, Feb 26, 2016
- Is zero-effort computer security a dream?, Peerlyst, Feb 26, 2016
- Is zero-effort computer security a dream?, The CyberSecurity Place, Feb 26, 2016
- Is zero-effort computer security a dream?, SpiceWorks, Feb 26, 2016
- Is zero-effort computer security a dream?, Threat Brief, Feb 26, 2016
- Is zero-effort computer security a dream?, Webroot, Feb 27, 2016
All Your Voices are Belong to Us
- AI-Powered Deep Fakes Are Supercharging Scams Across Industries, TheMessenger, Aug 22, 2023
- Necromancy? Big Tech Giant Amazon Uses AI To Bring Voices Of Dead Relatives To Life, Christianity Daily, June 28, 2022
- 50 States of Voice [Part 1 of 5], This Week In Voice VIP, Oct 15, 2020.
- If it Quacks Like a Duck, Communications of the ACM, Mar 26, 2020.
- Baidu can clone your voice after hearing just a minute of audio, New Scientist, Feb 26, 2018
- Baidu can clone your voice after hearing just a minute of audio, Daily News, Feb 26, 2018 [pdf]
- In den Mund gelegt, Feb 11, 2018
-
How Criminals Can Use Video and Voice To Assume Your Identity, WVXU, Cincinnati Edition , Aug 28, 2017
- Your Phone Compass Can Stop Voice Hacks for This Scientific Reason, Inverse Innovation, Jun 7, 2017
- Pillanatok alatt saját hangunkon beszélhet a mesterséges intelligencia, Bitport, Apr 27, 2017
- Sinister startup claims it can imitate any voice in just one minute, The INQUIRER, Apr 25, 2017
- Imitating people’s speech patterns precisely could bring trouble,The Economist, Apr 20, 2017
- Voice Hackers Can Record Your Voice Then Use Morpher To Trick Authentication Systems, Linkedin, Oct 18, 2015
- Automated voice can fool humans, machines, Bangalore Mirror, Oct 2, 2015
- Voice hackers can record your voice then use morpher to trick authentication systems, The Rumor Mill News, Oct 2, 2015
- UAB research finds automated voice imitation can fool humans and machines, UAB News, Sep 25, 2015
- Research Finds Automated Voice Imitation Can Fool Humans and Machines, Communications of the ACM, Sep 28, 2015
- UAB Research Finds Automated Voice Imitation Can Fool Humans and Machines, ACM TechNews, Sep 30, 2015
- Voice hackers can record your voice then use morpher to trick authentication systems, Network World, Sep 30, 2015
- UAB researchers find that automated voice imitation can spoof voice authentication systems, Biometric Update, Sep 28, 2015
- Hackers can imitate your voice to trick authentication systems, The Stack, Sep 28, 2015
- Automated Voice Imitation fools Humans and Machines, Scientific Computing, Sep 29, 2015
- Voice-based user authentication is not as secure as we thought, ITProPortal, Sep 29, 2015
- Research finds automated voice imitation can fool humans and machines, PHYS ORG, Sep 28, 2015
- Experts warn of morphing threat to voice biometrics, Planet Biometric, Sep 28, 2015
- How hackers could steal your voice to access your bank account, International Business Times, Sep 28, 2015
- Biometrics: Advances Smack Down Workarounds, Bank Info Security, Sep 29, 2015
- Hackers steal your voice, Tech Eye Net, Sep 29, 2015
- Security-Systeme mit Stimmkopie ausgetrickst, Presstext, Sep 29, 2015
Transparent Gestures
- UAB rolls out new technology to help users combat mobile malware attacks, UAB, Mar 26, 2015
- New mobile-malware detection technique uses gestures, COPMUTERWORLD, Mar 27, 2015
- New mobile-malware detection technique uses gestures, PCWorld, Mar 27, 2015
- New mobile-malware detection technique uses gestures, CIO, Mar 27, 2015
- New technology to help users combat mobile malware attacks, Phys.org, Mar 27, 2015
- University Rolls Out New Technology to Help Users Combat Mobile Malware Attacks, Lab Manager, Mar 30, 2015
- New Technique Uses Gestures To Detect Malware on Mobile Devices, On Click Info, Mar 30, 2015
- UAB Rolls Out New Technology to Help Users Combat Mobile Malware Attacks, Newswise, Mar 26, 2015
- Mobile security technology provides a malware protection boost, Mobile Commerce PRESS, Apr 1, 2015
- Everyday hand motions could protect smartphones from breaches, research shows, Fierce Mobile Government, Apr 1, 2015
VoIP Security (Crypto Phones)
- Users their own worst enemy when it comes to encrypted messaging apps, Graham Cluley, Dec 18, 2015
- User Error Compromises Many Encrypted Communication Apps, MIT Technology Review, Dec 14, 2015
- Dumb Human Errors Can Undermine the Security of Encrypted Communication Apps, Gizmodo, Dec 15, 2015
- User Errors Often Compromise Encryption, Schneier on Security, Dec 17, 2015
- Human error reduces security offered by encryption apps, Net Security, Dec 18, 2015
- University Researchers Discover Security Flaws in VoIP ‘Crypto Phones’, EdTech, Nov 26, 2014
- Cisco funds university research into VoIP security, Networked World, Nov 12, 2014
- Mobile VoIP Security Vulnerable to Mimicry Attacks, CACM News, Nov 6, 2014
- New research shows vulnerability in mobile phones’ applications offering voice communication security, Science Daily, Nov 5, 2014
- New research shows vulnerability in mobile phones’ applications offering voice communication security, Phys.org, Nov 6, 2014
- VoIP ‘Crypto’ Phones Can Be Fooled by Voice Impersonation, VOIP Monitoring Zone, Dec 3, 2014
- Wiretapping via Mimicry: UAB Research Highlights a Fundamental Vulnerability of a Secure Communication Technology, UAB News, Nov 5, 2014
- How secure is Skype? UAB gets $150K to improve VoIP security. Birmingham Business Journal, July 19, 2013
- UAB research to improve online communication security, UAB News, July 17, 2013
CAPTCHA
- Beyond CAPTCHA: A Better Way to Tell Humans and Robots Apart, OZY, Sep 29, 2014
- Research Unveils Improved Method To Let Computers Know You Are Human , Slashdot, Aug 19, 2014
- New Research Presents an Improved Method to Let Computers Know You Are Human , ACM TechNews, Aug 20, 2014
- Game-Like CAPTCHA Lets Computers Know You Are Human, Communications of the ACM, Aug 26, 2014
- Better than CAPTCHA: Improved method to let computers know you are human, ScienceDaily, Aug 25, 2014
- Researchers Devise a Better Way to CAPTCHA ,CIO, Sep 11, 2014
- CAPTCHAs Might Soon Be Out , IQpill, Aug 26, 2014
- New research presents an improved method to let computers know you are human, TECHSPOT, Aug 24, 2014
- DCG CAPTCHA – УЛУЧШЕННЫЙ СПОСОБ УЗНАТЬ КОМПЬЮТЕРУ ЧТО ПЕРЕД НИМ ЧЕЛОВЕК, TECHNEWS.RU, Aug 27, 2014
- Onderzoekers ontwikkelen betere CAPTCHA-variant, security.nl, Aug 19, 2014
- Ученые создали новый метод распознавания человека компьютером Источник, Центр, Aug 20, 2014
- Better than CAPTCHA: Improved method to let computers know you are human, Technocrat Epiphanies, Aug 26, 2014
- Saxena awarded nearly $75,000 to study CAPTCHA mechanisms, UAB News, Sep 17, 2014
- New research presents an improved method to let computers know you are human, UAB News, Aug 18, 2014
Contextual and Payment Security
- Jefferson County works to expand contact tracing, CBS42, Apr 23, 2020.
- Forget passwords: This is the future of logging in, CNBC, Aug 25, 2014
- UAB researchers work on next-gen security methods, Alabama’s 13, June 3, 2014
- Passwords no more? Researchers develop mechanisms that enable users to log in securely without passwords, Phys.org, June 4, 2014
- Passwords No More? UAB Researchers Develop Mechanisms That Enable Users to Log in Securely Without Passwords, Newswise, June 4, 2014
- Passwords No More? Mechanisms Enables Users to Log in Securely Without Passwords, Science Daily, June 4, 2014
- Logging in securely without passwords, Homeland Security News Wire, June 5, 2013
- UAB researchers could kill the password as we know it, Birmingham Business Journal, June 5, 2014
- New mechanism allows users to log in to their terminals without inputting a password, Electronic Products, June 5, 2014
- Indian-origin scientist working on a system to end passwords, The Times of India, June 5, 2014
- Passwords No More? Communications of the ACM, June 5, 2014
- UAB researching technological alternative to online passwords, Myfoxal, June 6, 2014
- UAB researchers seek easy, hacker-proof way for users to open their cars, computers, other gadgets, Alabama Local News, June 10, 2014
- Interview With Dr. Nitesh Saxena, Beyond The Computer Password, Crush Plate, June 10, 2014
- Passwords? Soon You May Log In Securely Without Them, ACM TechNews, June 11, 2014
- Future credit cards could thwart Target hackers, Yahoo! Finance, December 23, 2013.
- System Improves Mobile Payment Security, Protects Personal Info. Communications of the ACM, Sep 12, 2012.
- Mobile Payments: A New Frontier for Criminals. Bloomberg BusinessWeek, Oct 4, 2012.
- Audio samples used to secure NFC authentication. ZDNet, Sep 19, 2012.
- Passwords? Soon you may log in securely without them, UAB News, June 3, 2014
- Saxena wins Google award for mobile security research, UAB News, Sep 19, 2013
- UAB creates system to bolster mobile payment security, personal info. NFC News, Sep 13, 2012.
- UAB system improves mobile payment security, protects personal info, UAB News, Sep 11, 2012
Two-Factor Authentication
- Strengthening Two-Factor Authentication, Industrial Safety and Security Source, March 5, 2014
- Ease and security of password protections improved, Science Daily, February 28, 2014
- New methods for password protection proposed, The Indian Express, March 3, 2014
- New methods for password protection proposed, The Hindustan Times, March 3, 2014
- Scientists propose new two-factor methods for password protection, NDTV, March 3, 2014
- New methods for password protection proposed, The Economic Times, March 3, 2014
- Password protection: Scientists propose new methods, The Times of India, March 3, 2014
- UAB research improves ease and security of password protections, UAB News, Feb 26, 2014
Mobile Malware
- How secure is Skype? UAB gets $150K to improve VoIP security. Birmingham Business Journal, July 19, 2013
- SPECIAL REPORT: When Malware Attacks (includes video interview). Fox 54 (WTVM), July 11, 2013
- Music, lighting can let hackers onto your phone. MSN News, May 29, 2013
- Cafe, Mall Music Could Trigger Malware. Discovery News, May 31, 2013
- Music playing 55 feet away could covertly activate Android mobile malware. Computer World, May 29, 2013
- Music is a Turn-On for Malware. Symantec, May 29, 2013
- Security boffins say music could trigger mobile malware. The Register, May 28, 2013
- Music, lighting or vibration could trigger mobile malware. Yahoo News, May 27, 2013
- Music and Movies Could Trigger Mobile Malware. Slashdot, May 20, 2013
- UAB Research Finds New Channels to Trigger Mobile Malware. ACM TechNews, May 16, 2013
- Beware, that music at Starbucks can be malware. The Times of India, May 27, 2013.
- Music, lighting or vibration could trigger mobile malware. The Hindustan Times, May 27, 2013
- Lights, Music Could Trigger Smartphone Malware. NBC News, May 20, 2013
- UAB develops malware defense for smartphones. Birmingham Business Journal, Mar 1, 2013
- On Your Side: New UAB app defends against malware. Fox 6 (WBRC), Mar 14, 2013
- UAB Develops a Simple Defense for Complex Smartphone Malware. ACM TechNews, Feb 28, 2013
- UAB develops a simple defense for complex smartphone malware, UAB News, Feb 28, 2013
- UAB research finds new channels to trigger mobile malware, UAB News, May 16, 2013
Miscellaneous
- Expectation of privacy in a digital world (video), ABC 33/40, February 13, 2014
- 13 INVESTIGATES: Wi-fi thieves. NBC 12, Feb 25, 2013
- Spies Like Us — Putting a New Spin on Computer Security, UAB Magazine, Apr 11, 2013