College Station, TX — June 2025
SHARE THIS
In groundbreaking research presented at the ACM Web Conference 2025 (WWW), researchers from Texas A&M University’s Security and Privacy in Emerging Computing and Networking Systems (SPIES) lab have highlighted significant vulnerabilities and accessibility challenges in two-factor (2FA) and passwordless authentication methods for blind and visually impaired users relying on screen readers.
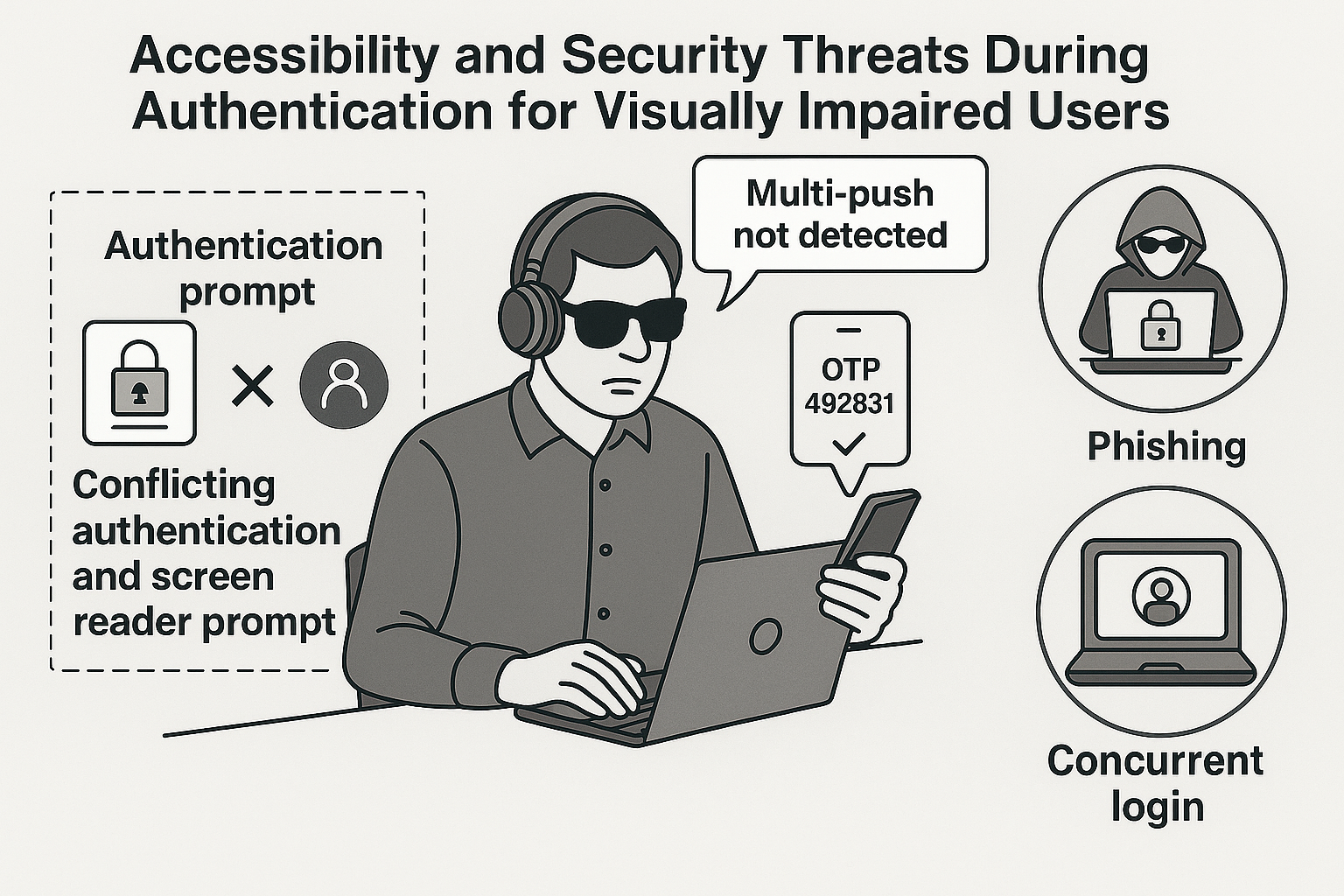
The study, titled “Broken Access: On the Challenges of Screen Reader Assisted Two-Factor and Passwordless Authentication,” reveals how commonly used authentication methods, such as Google, Microsoft, and Duo’s OTP-2FA, phone call 2FA, push notifications, and FIDO-based MFA, often fail to effectively accommodate the specific needs of blind and visually impaired individuals. Through systematic evaluation using the team’s newly developed Authentication Workflows Accessibility Review and Evaluation (AWARE) framework, researchers found numerous critical security issues, including susceptibility to phishing, notification fatigue, and concurrent login attacks.
Key findings highlight how imprecise instructions and insufficient accessibility considerations significantly increase vulnerability for visually impaired users. Specifically, the researchers identified critical conflicts between simultaneous authentication steps (such as receiving OTP codes via phone calls) and screen reader audio prompts, leading to confusion and potential security breaches. Additionally, they discovered screen readers mispronouncing numeric OTPs, interpreting them incorrectly as continuous numbers rather than distinct digits, and observed difficulties in managing authentication prompts when users concurrently used screen readers on both smartphones and PCs.
This research underscores the urgent need for developers to implement clearer authentication workflows and better integration of accessibility standards. The SPIES team offers concrete recommendations for enhancing security and usability, such as explicit instructions, automated phishing detection, and optimized communication between authentication interfaces and screen readers.
The findings presented at WWW ’25 are a pivotal step toward ensuring digital authentication methods are secure and inclusive for all users, particularly the visually impaired.
To read the full paper, click here.
Citation:
Md Mojibur Rahman Redoy Akanda, Ahmed Tanvir Mahdad, and Nitesh Saxena. 2025. Broken Access: On the Challenges of Screen Reader Assisted Two-Factor and Passwordless Authentication. In Proceedings of the ACM Web Conference 2025 (WWW ’25), April 28–May 2, 2025, Sydney, NSW, Australia. ACM, New York, NY, USA, 13 pages. https://doi.org/10.1145/3696410.3714579
Read more stories like this on AI Spies News.
Follow us on Medium.