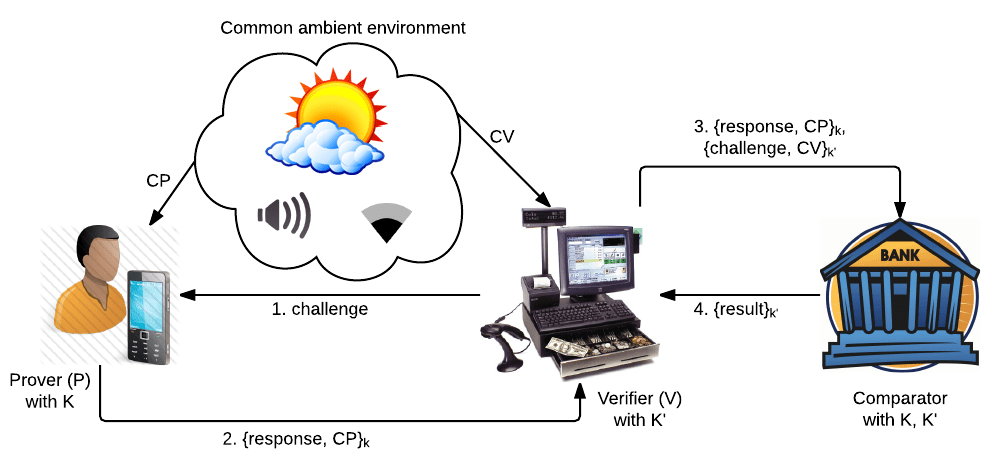
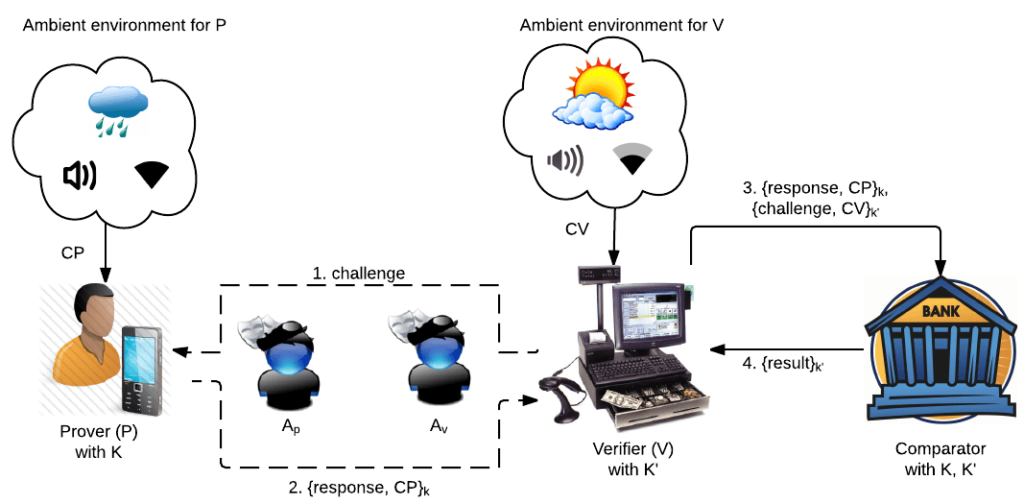
Zero-Interaction Authentication (ZIA) refers to approaches that authenticate a user to a verifier (terminal) without any user interaction. Currently deployed ZIA solutions are predominantly based on the terminal detecting the proximity of the user’s personal device, or a security token, by running an authentication protocol over a short-range wireless communication channel. Unfortunately, this simple approach is highly vulnerable to low-cost and practical relay attacks which completely offset the usability benefits of ZIA. The use of contextual information, gathered via on-board sensors, to detect the co-presence of the user and the verifier is a recently proposed mechanism to resist relay attacks.
As a case in point, we systematically investigate the performance of different sensor modalities for co-presence detection with respect to a standard Dolev-Yao adversary. We compare the performance of four commonly available sensor modalities (Wi-Fi, Bluetooth, GPS, and Audio) in resisting ZIA relay attacks. Further, we compare four new ambient environment sensor modalities, ambient temperature, precision gas, humidity, and altitude utilizing an off-the-shelf device called Sensordrone. Then, we show that, compared to any single modality, fusing multiple modalities improves resilience against ZIA relay attacks while retaining a high level of usability. Finally, we motivate the need for a stronger adversarial model to characterize an attacker who can compromise the integrity of context sensing itself. We show that in the presence of such a powerful attacker, each individual sensor modality offers very low security. Positively, the use of multiple sensor modalities improves security against such an attacker if the attacker cannot compromise multiple modalities simultaneously.
People
Faculty
Student
- Babins Shrestha (PhD student; Now Sr. Information Security Analyst at VISA Inc.)
External Collaborators:
- Xiang Gao (MS student; University of Helsinki; Now Software Engineer at LiveRing)
- Hien Thi Thu Truong (Postdoctoral Researcher; University of Helsinki; Now Research Scientist at NEC Laboratories Europe GmbH)
- Petteri Nurmi (Senior Researcher; University of Helsinki; Now Lecturer at Lancaster University)
- N. Asokan (Professor; Aalto University and University of Helsinki)
Publication
- Sensor-based Proximity Detection in the Face of Active Adversaries
Babins Shrestha, Nitesh Saxena, Hien Truong and N. Asokan.
In IEEE Transactions on Mobile Computing (TMC),
[pdf] - Drone to the rescue: Relay-resilient authentication using ambient multi-sensing
Babins Shrestha, Nitesh Saxena, Hien Thi Thu Truong, N Asokan
International Conference on Financial Cryptography and Data Security (FC), March 2014
[pdf] - Comparing and fusing different sensor modalities for relay attack resistance in zero-interaction authentication
Hien Thi Thu Truong, Xiang Gao, Babins Shrestha, Nitesh Saxena, N Asokan, Petteri Nurmi
IEEE International Conference on Pervasive Computing and Communications (PerCom), March 2014
[pdf] - Using contextual co-presence to strengthen Zero-Interaction Authentication: Design, integration and usability
Hien Thi Thu Truong, Xiang Gao, Babins Shrestha, Nitesh Saxena, N Asokan, Petteri Nurmi
Pervasive and Mobile Computing (PMC), Vol: 16, 2015
[doi]