Crypto Phones represent an important approach for end-to-end VoIP security, claiming to prevent “wiretapping” and session hijacking attacks without relying upon third parties. For slightly more detail about Crypto Phones please refer to our Wiretapping Via Mimicry project or the following figure.
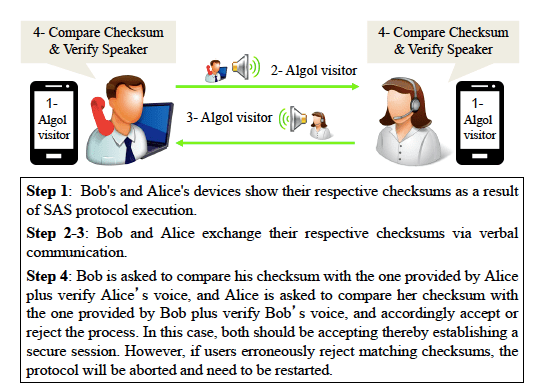
Figure 1: Crypto Phones benign setting – original voices; matching SAS (this is the setting subject to our usability assessment).
In order to establish a secure session, Crypto Phones rely upon end users to perform two tasks: (1) checksum comparison: verbally communicating and matching short checksums displayed on users’ devices, and (2) speaker verification: ascertaining that the voice announcing the checksum is the voice of the legitimate user at the other end. However, the human errors in executing these tasks may adversely affect the security and usability of Crypto Phones. Particularly, failure to detect mismatching checksums or imitated voices would result in a compromise of Crypto Phones session communications.
We present a human factors study, with 128 online participants, investigating the security and usability of Crypto Phones with respect to both checksum comparison and speaker verification. To mimic a realistic VoIP scenario, we conducted our study using the WebRTC platform where each participant made a call to our IVR server via a browser, and was presented with several challenges having matching and mismatching checksums, spoken in the legitimate user’s voice, different speakers’ voices and automatically synthesized voices. Our results show that Crypto Phones offer a weak level of security (significantly weaker than that guaranteed by the underlying protocols), and their usability is low (although might still be acceptable). Quantitatively, the overall average likelihood of failing to detect an attack session was about 25-50%, while the average likelihood of accepting a legitimate session was about 75%. Moreover, while the theory promises an exponential increase in security with increase in checksum size, we found a degradation in security when moving from 2-word checksum to 4-word checksum.
People
Faculty
Student
- Maliheh Shirvanian (PhD candidate)
Publication
- On the security and usability of crypto phones.
Maliheh Shirvanian, Nitesh Saxena.
In the Annual Computer Security Applications Conference (ACSAC), December, 2015.
[pdf]
Media Coverage
- Users their own worst enemy when it comes to encrypted messaging apps, Graham Cluley, Dec 18, 2015
- User Error Compromises Many Encrypted Communication Apps, MIT Technology Review, Dec 14, 2015
- Dumb Human Errors Can Undermine the Security of Encrypted Communication Apps, Gizmodo, Dec 15, 2015
- User Errors Often Compromise Encryption, Schneier on Security, Dec 17, 2015
- Human error reduces security offered by encryption apps, Net Security, Dec 18, 2015
- University Researchers Discover Security Flaws in VoIP ‘Crypto Phones’, EdTech, Nov 26, 2014
- Cisco funds university research into VoIP security, Networked World, Nov 12, 2014
- Mobile VoIP Security Vulnerable to Mimicry Attacks, CACM News, Nov 6, 2014
- New research shows vulnerability in mobile phones’ applications offering voice communication security, Science Daily, Nov 5, 2014
- New research shows vulnerability in mobile phones’ applications offering voice communication security, Phys.org, Nov 6, 2014
- VoIP ‘Crypto’ Phones Can Be Fooled by Voice Impersonation, VOIP Monitoring Zone, Dec 3, 2014
- Wiretapping via Mimicry: UAB Research Highlights a Fundamental Vulnerability of a Secure Communication Technology, UAB News, Nov 5, 2014
- How secure is Skype? UAB gets $150K to improve VoIP security. Birmingham Business Journal, July 19, 2013
- UAB research to improve online communication security, UAB News, July 17, 2013
