Vulnerabilities of Existing Designs, and Countermeasures
Based on the notion of “emergence”, Xu et al. (Usenix Security 2012; TDSC 2013) developed the first concrete instantiation of emerging-image moving-object (EIMO) CAPTCHAs using 2D hollow objects (codewords), shown to be usable and believed to be secure. In this work, we highlight the hidden security weaknesses of such a 2D EIMO CAPTCHA design. A key vulnerability is that the camera projection on 2D objects is constant (unlike 3D objects), making it possible to reconstruct the underlying codewords by superimposing and aggregating the temporally scattered parts of the object extracted from consecutive frames. We design and implement an automated attack framework to defeat this design using image processing techniques, and show that its accuracy in recognizing moving codewords is up to 89.2%, under different parameterizations. Our framework can be broadly used to undermine the security of different instances of 2D EIMO CAPTCHAs (not just the current state-of-the-art by Xu et al.), given the generalized and robust back-end theories in our attack, namely the methods to locate a codeword, reduce noises and accumulate objects’ contour information from consecutive frames corresponding to multiple time periods. As a countermeasure, we propose a fundamentally different design of EIMO CAPTCHAs based on pseudo 3D objects, and examine its security as well as usability. We argue that this design can resist our attack against 2D EIMO CAPTCHAs, although at the cost of reduced usability compared to the – now insecure –2D EIMO CAPTCHAs.
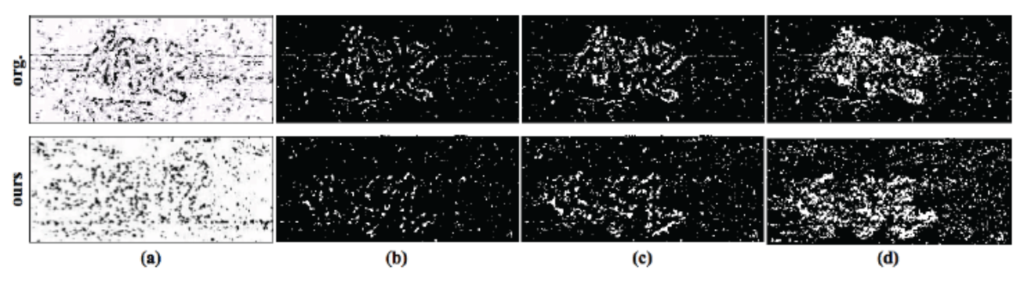
Comparison between the original EI-Nu CAPTCHA and our design with codeword “KHZ”. (a) A single frame image. (b) A single binary mask after removing the background scene. (c) Superimposition of 2 consecutive binary masks. (d) Superimposition of 5 consecutive binary masks.
People
Faculty
Student
- Song Gao (@UAB; PhD 2014; now Software Engineer at Google)
- Manar Mohamed (@UAB; PhD 2016; now Visiting Assistant Professor at Miami University)
Publication
- Emerging-Image Motion CAPTCHAs: Vulnerabilities of Existing Designs, and Countermeasures
Song Gao, Manar Mohamed, Nitesh Saxena, and Chengcui Zhang.
In IEEE Transactions on Dependable and Secure Computing (TDSC), 2017.
[pdf]
