Keystroke Emanations & Side Channel Attacks
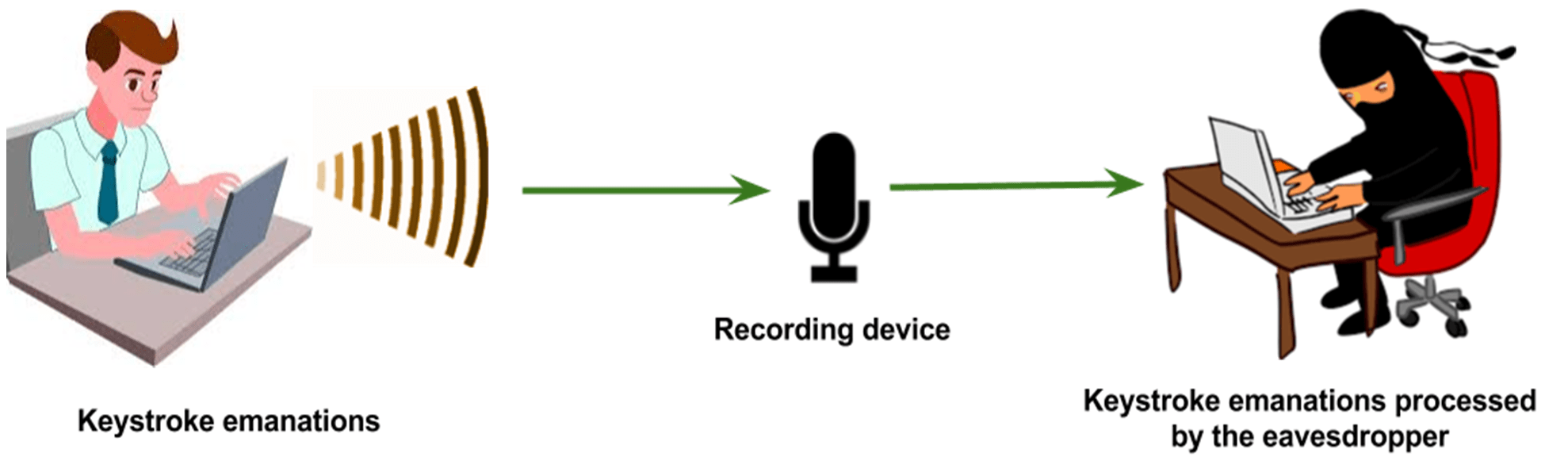
Keystroke emanations have been found to leak information through side channels. This information can be exploited via side channel attacks for nefarious purpose. Such attacks fall in the category of side channel attacks that tend to exploit the physical implementation of the deployed security mechanism rather than using brute force or algorithmic weakness inherent in the mechanism.
We have set out to investigate acoustic side channel attacks using keystroke emanations in the context of passwords and other sensitive information (e.g. credit card data, SSN, ATM PIN). We study these attacks in different scenarios that closely resemble real world situations. We also explore remote eavesdropping scenarios where VoIP applications can be exploited to overhear the keystroke emanations that can later be used to extract confidential information.
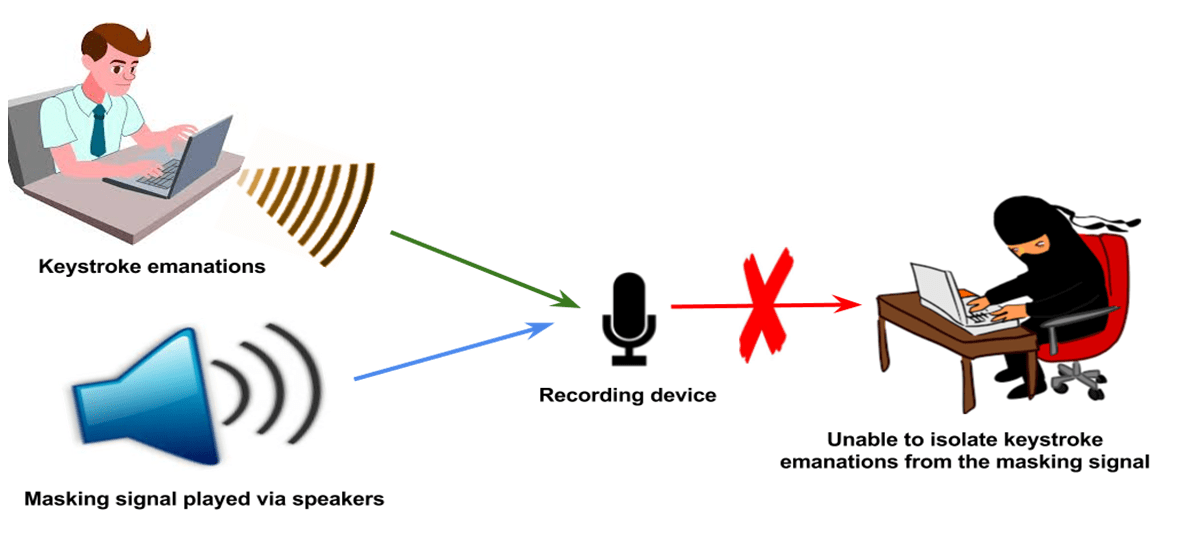
We also focus on designing a competent defense system that can help contain the privacy breach due to side channel attacks. For acoustic side channel attack, we are researching signal-masking techniques that can cloak the keystroke emanations making it hard for an attack to exploit the audio leakage due to the emanations. The masking signal is played as a background noise at an appropriate volume for decreasing the signal to noise ratio, making it harder to isolate the keystroke emanations. Such defense measures are also tested for their effectiveness under multiple scenarios and for their usability, as the users should not be distracted from their work while the masking signal is being played.
People
Faculty
Student
- S Abhishek Anand (PhD candidate)
Publication
- Keyboard Emanations in Remote Voice Calls: Password Leakage and Noise(less) Masking Defenses.
Abhishek Anand and Nitesh Saxena
In ACM Conference on Data and Application Security and Privacy (CODASPY), March 2018..
[pdf] - A Sound for a Sound: Mitigating Acoustic Side Channel Attacks on Password Keystrokes with Active Sounds.
S Abhishek Anand and Nitesh Saxena.
In Financial Cryptography and Data Security(FC16), February 2016.
[pdf]
Media Coverage
- Research proposes background noise to prevent side channel attacks on computer keyboards, TechXplore, Sep 27, 2016
- Research proposes background noise to prevent side channel attacks on computer keyboards, UAB News, Sep 26, 2016
- Research proposes background noise to prevent side channel attacks on computer keyboards, WN.com, Sep 26, 2016
- Research proposes background noise to prevent side channel attacks on computer keyboards, Voat, Sep 27, 2016
- The next cyberattack could come from sound waves, The Conversation, March 27, 2017
- The next cyberattack could come from sound waves, Yahoo! Tech, March 27, 2017
- Sound waves being used to launch cyber attacks!, Cybersecurity Insiders, March 27, 2017
- Commentary: The next cyberattack could come from sound waves, CHANNEL NEWSASIA, March 29, 2017
- The next cyberattack could render your anti-virus and encryption software useless, Business Insider, March 27, 2017