Pitfalls in Designing Zero-Effort Deauthentication: Opportunistic Human Observation Attacks.
Deauthentication is an important component of any authentication system. The widespread use of computing devices in daily life has underscored the need for zero-effort deauthentication schemes. However, the quest for eliminating user effort may lead to hidden security flaws in the authentication schemes.
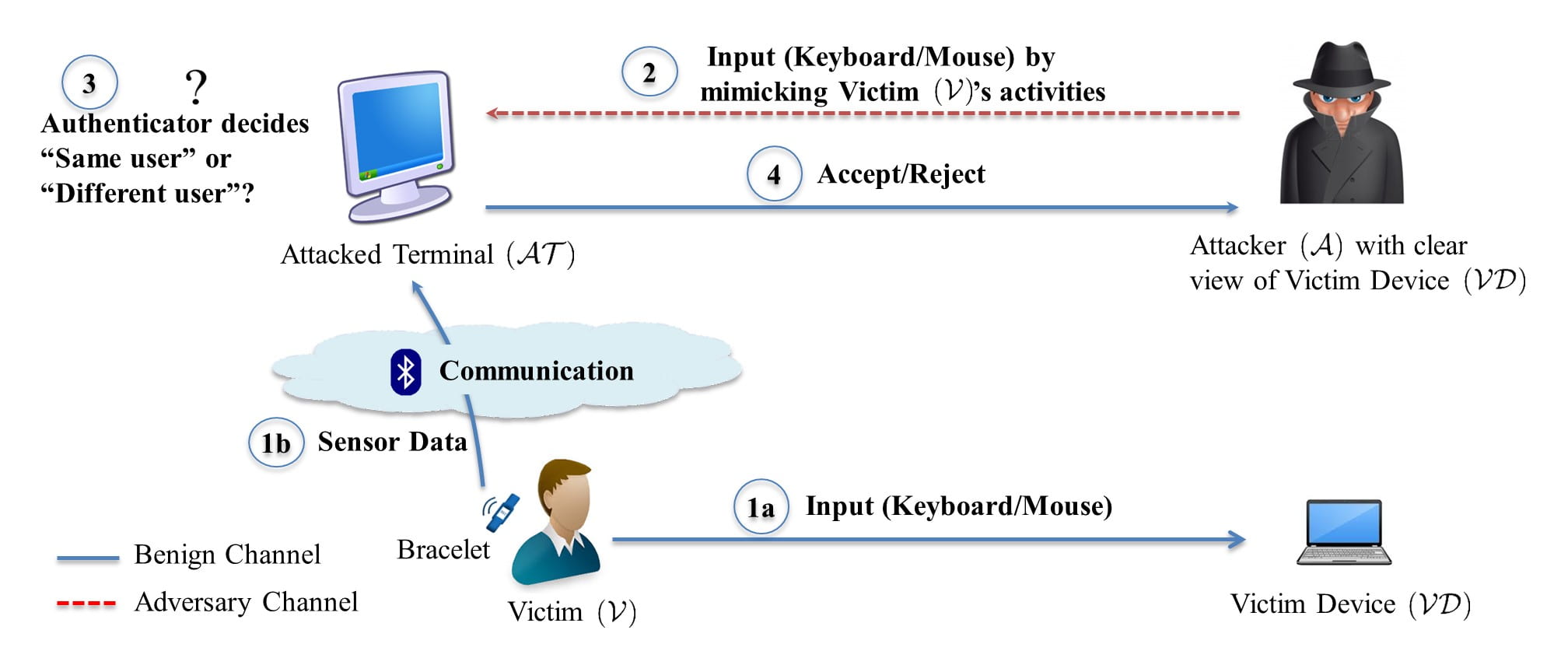
As a case in point, we investigate a prominent zero-effort bilateral deauthentication scheme called ZEBRA, which provides an interesting and a useful solution to a difficult problem as demonstrated in the original paper. ZEBRA is intended for scenarios where users authenticate to “terminals” (such as desktop computers). In such scenarios, users typically have to either manually deauthenticate themselves by logging out or locking the terminal, or the terminal can deauthenticate a user automatically after a sufficiently long period of inactivity. The former requires user effort while the latter sacrifices promptness. ZEBRA attempts to make the process of deauthentication both prompt and transparent: once a user is authenticated to a terminal (using say a password), it continuously, yet transparently re-authenticates the user so that prompt deauthentication is possible without explicit user action. A user is required to wear a bracelet equipped with sensors on his mouse holding hand. The bracelet is wirelessly connected to the terminal, which compares the sequence of events it observes (e.g., keyboard/mouse interactions) with the sequence of events inferred using measurements from the bracelet sensors. The logged-in user is deauthenticated when the two sequences no longer match.
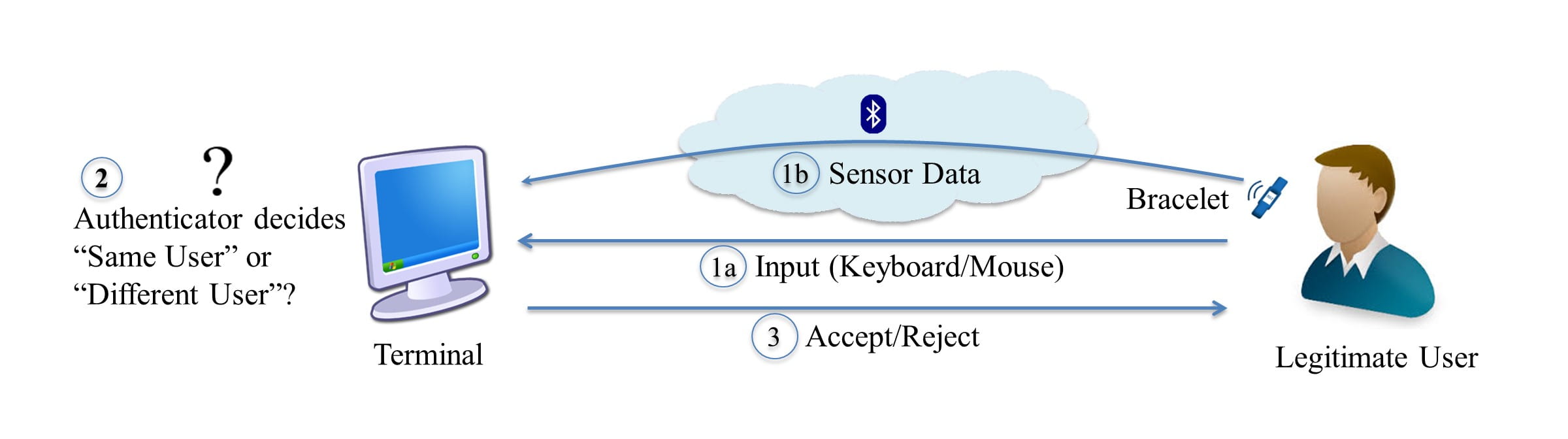
Figure1 : Normal operation of ZEBRA [Mare et al.; Oakland’14]
ZEBRA is particularly compelling because of its simplicity of design. However, the simplicity hides a design assumption that an adversary can exploit to defeat the scheme. We show how a more realistic adversary can circumvent ZEBRA. We identify a subtle incorrect assumption in its adversary model that leads to a fundamental design flaw. We exploit this to break the scheme with a class of attacks (Figure 2 shows the basic attack settings) that are much easier for a human to perform in a realistic adversary model, compared to the naive attacks studied in the ZEBRA paper. For example, one of our main attacks, where the human attacker has to opportunistically mimic only the victim’s keyboard typing activity at a nearby terminal, is significantly more successful compared to the naive attack that requires mimicking keyboard and mouse activities as well as keyboard-mouse movements. Further, by understanding the design flaws in ZEBRA as cases of tainted input, we show that we can draw on well-understood design principles to improve ZEBRA’s security.
People
Faculty
Student
- Prakash Shrestha (PhD student)
External Collaborators:
- Otto Huhta (PhD student; Aalto University; Now Master Expert at Nordea)
- Swapnil Udar (MS student; Aalto University; Now Sr. Software Engineer at TomTom)
- Mika Juuti (PhD student; Aalto University)
- N. Asokan (Professor; Aalto University and the University of Helsinki)
Publications
- Beware of Your Vibrating Devices! Vibrational Relay Attacks on Zero-Effort Deauthentication
Prakash Shrestha and Nitesh Saxena.
In International Conference on Applied Cryptography and Network Security (ACNS), June 2022 - Pitfalls in Designing Zero-Effort Deauthentication: Opportunistic Human Observation Attacks.
Otto Huhta, Prakash Shrestha, Swapnil Udar, Mika Juuti, Nitesh Saxena and N. Asokan.
In the Network and Distributed System Security Symposium (NDSS), February 2016.
[pdf]
Media Coverage
- Is zero-effort computer security a dream? Breaking a new user verification system, UAB News, Feb 24, 2016
- Is zero-effort computer security a dream? Breaking a new user verification system, Science Daily, Feb 24, 2016
- Is Zero-Effort Computer Security a Dream? Breaking a New User Verification System, Newswise, Feb 24, 2016
- Is zero-effort computer security a dream? Breaking a new user verification system, Tech Xplore, Feb 25, 2016
- Is Zero-effort Computer Security a Dream? Breaking a New User Verification System, Scientific Computing, Feb 25, 2016
- Is zero-effort computer security a dream? Breaking a new user verification system, Sci24H.com, Feb 25, 2016
- Is zero-effort computer security a dream?, Help Net Security, Feb 26, 2016
- Is zero-effort computer security a dream?, IT Security News, Feb 26, 2016
- Is zero-effort computer security a dream?, Peerlyst, Feb 26, 2016
- Is zero-effort computer security a dream?, The CyberSecurity Place, Feb 26, 2016
- Is zero-effort computer security a dream?, SpiceWorks, Feb 26, 2016
- Is zero-effort computer security a dream?, Threat Brief, Feb 26, 2016
- Is zero-effort computer security a dream?, Webroot, Feb 27, 2016