Defense against Smartphone Keyloggers
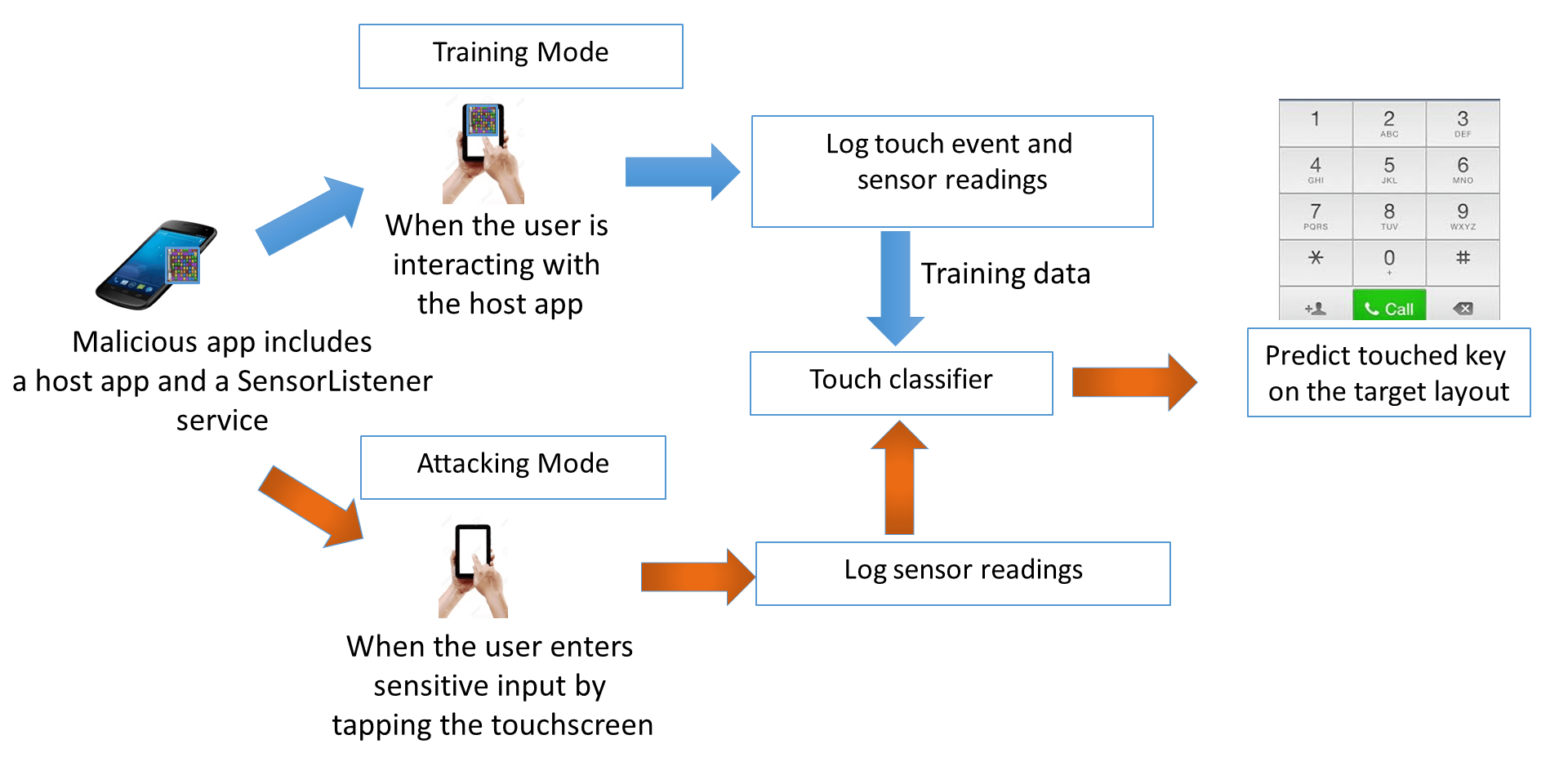
Recent research shows that it is possible to infer a user’s touchscreen inputs (e.g., passwords) on Android devices based on inertial (motion/position) sensors, currently freely-accessible by any Android app. Figure below shows the high level steps involved in motion based touchstroke logging attack. Given the high accuracies of such touchstroke logging attacks, they are now considered a significant threat to user privacy. Consequently, the security community has started exploring defenses to such side channel attacks, but the suggested solutions are either not effective (e.g., those based on vibrational noise) and/or may significantly undermine system usability (e.g., those based on keyboard layout randomization).
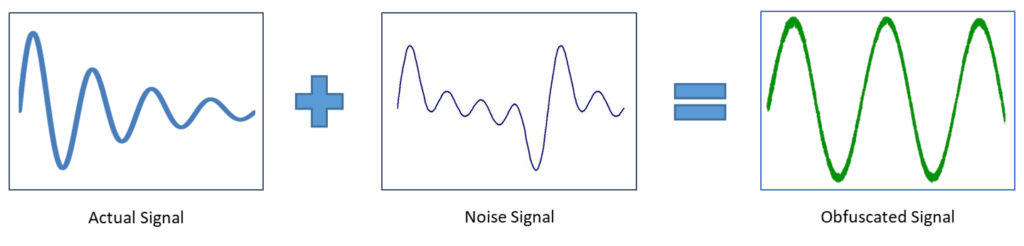
In this work, we introduce a novel and practical defense to motion-based touchstroke leakage based on system-generated, fully automated and user-oblivious sensory noise. Our defense leverages a recently developed framework, SMASheD, that takes advantage of the Android’s ADB functionality and can programmatically inject noise to various inertial sensors. Although SMASheD was originally advertised as a malicious app by its authors, we use it to build a defense mechanism, called Slogger (“Smashing the logger”), for defeating sensor-based touchstroke logging attacks. Slogger transparently inserts noisy sensor readings in the background as the user provides sensitive touchscreen input (e.g., password, PIN or credit card info) in order to obfuscate the original sensor readings. It can be installed in the user space without the need to root the device and to change the device’s OS or kernel. The figure below shows the notion of noise injection to obfuscate the original signal.
People
Faculty
Student
- Prakash Shrestha (PhD student)
- Manar Mohamed (@UAB; PhD 2016; instructional faculty of Computer Science at the Temple University)
Publication
- Slogger: Smashing Motion-based Touchstroke Logging with Transparent System Noise.
Prakash Shrestha, Manar Mohamed and Nitesh Saxena
In ACM Conference on Wireless Network Security (WiSec), July 2016
[pdf]
Media Coverage
- Research finds novel defense against sophisticated smartphone keyloggers, UAB News, Sept 02, 2016
- UAB researchers find way around malicious attacks on Android devices, Birmingham Business Journal, Sept 08, 2016
- UAB researchers find way around malicious attacks on Android devices, Tuscaloosa News.Net, Sept 09, 2016
- Research finds novel defense against sophisticated smartphone keyloggers , Wn.com, Sept 02, 2016
- Research Finds Novel Defense Against Sophisticated Smartphone Keyloggers, Public., Sept 02, 2016
- Research finds novel defense against sophisticated smartphone keyloggers, TechXplore, Sept 05, 2016