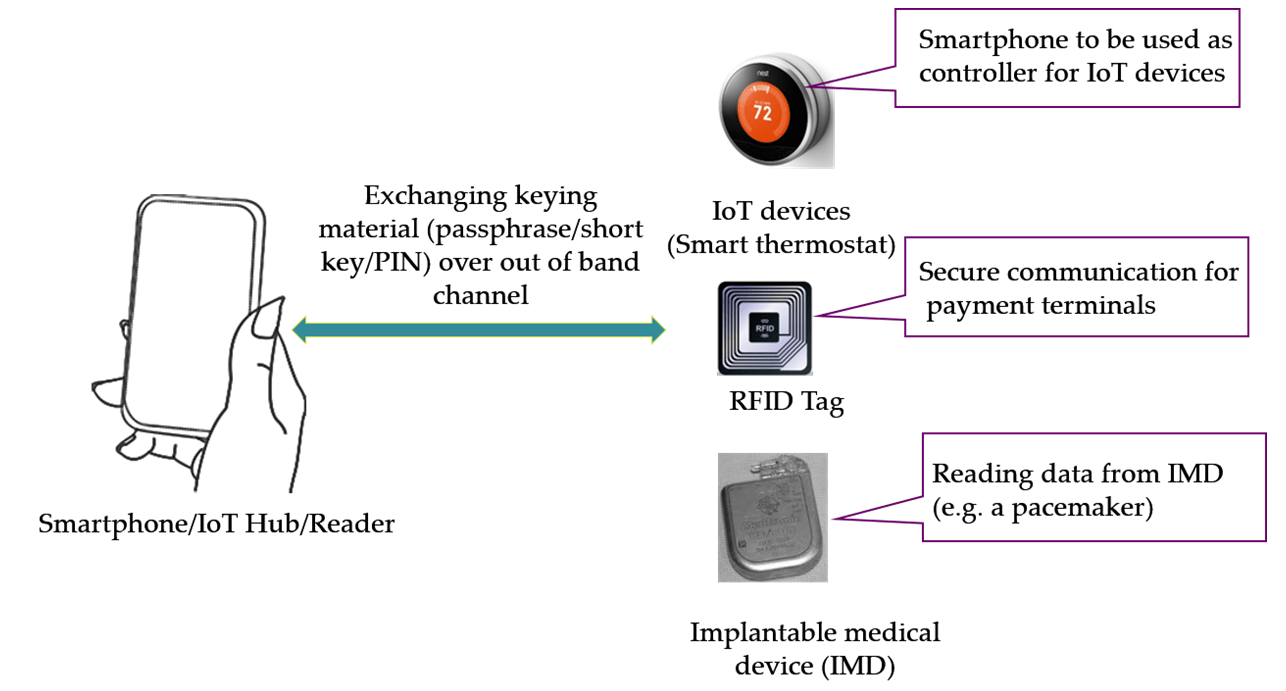
Pairing between wireless devices may be secured by the use of an auxiliary channel such as audio, visual or vibrations. A simple approach to pairing involves one of the devices initiating the transmission of a key, or keying material like a short password, over a vibration channel to the other device. This approach is efficient (only unidirectional transfer is needed) and simple (the sending device requires an embedded vibration motor and receiving device requires an accelerometer sensor). A successful pairing is achieved when the receiving device is able to decode the key without any errors while any eavesdropper attacker is unable to eavesdrop the key.
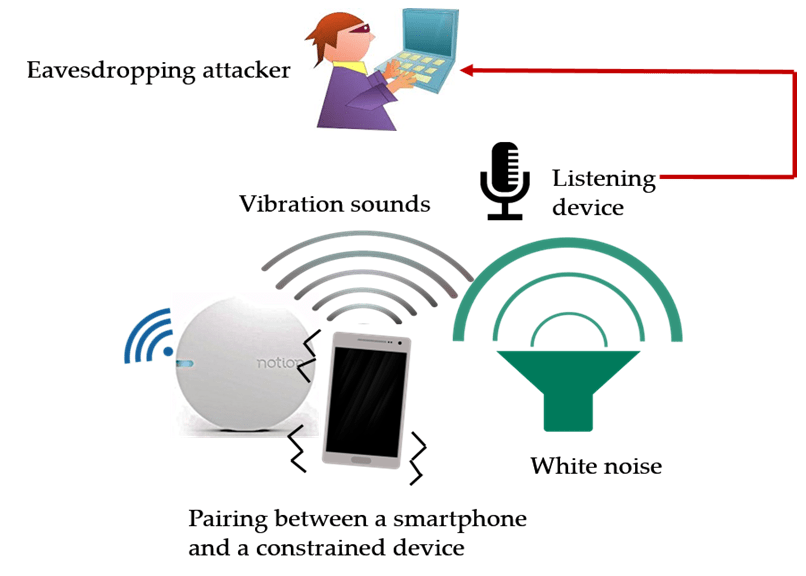
We pursue a systematic investigation of the security of vibration channel against an eavesdropping attacker. Recent work suggests sending the keying material over a clear vibrational channel poses a significant risk of an acoustic side channel attack. Specifically, an adversary can listen onto the acoustic sounds generated by the vibration motor of the sending device and infer the keying material with a high accuracy. To counteract this threat, we aim to design a novel pairing scheme, called Vibreaker (a “Vibrating speaker”), that involves active injection of acoustic noise in order to mask the key signal. In this scheme, the sending device artificially injects noise in the otherwise clear audio channel while transmitting the keying material via vibrations. The scheme requires no additional effort by the user, and imposes minimum hardware requirement and hence can be applied to many different contexts, such as pairing of IoT and implanted devices, wearables and other commodity gadgets.
We also examine the prospect of a co-resident eavesdropping model where the eavesdropper is co-located with the victim device(s). We found out that such an attacker is able to breach noisy vibration pairing such as Vibreaker due to inefficiency of current hardware present on constrained wireless devices. We aim to enhance the existing noisy vibrational pairing by adding low frequency tones that will cloak the footprints of vibration sounds at sub 500Hz frequency bands. We also study the usability of the enhanced masking signal and its effect on the decoding ability of the receiving device.
People
Faculty
Student
- S Abhishek Anand (PhD candidate)
Publication
- Noisy Vibrational Pairing of IoT Devices
Abhishek Anand, and Nitesh Saxena
In IEEE Transactions on Dependable and Secure Computing (TDSC), Special Issue on Emerging Attacks and Solutions for Secure Hardware in the Internet of Things, 2018.
[pdf] - Coresident Evil: Noisy Vibrational Pairing in the Face of Co-located Acoustic Eavesdropping.
S Abhishek Anand and Nitesh Saxena.
In 10th ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec), 2017.
[pdf] - Vibreaker: Securing Vibrational Pairing with Deliberate Acoustic Noise.
S Abhishek Anand and Nitesh Saxena.
In 9th ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec), 2016.
[pdf]