Masking Sound-based Opportunistic Attacks in Zero-Effort Deauthentication
Deauthentication is an important component of any computing system that promises to offer legitimate access to restricted services residing on the system. As computing devices are ubiquitous, it has underscored the need to design zero-effort deauthentication systems from a usability perspective. While the design of such deauthentication systems is geared towards making them more usable, often the security implication of these deigns overlook the physical security of the system resulting in various side channel vulnerabilities in the system. This issue highlights the need to design a defense mechanism that is capable of minimizing the threat posed by such side channel attacks while having minimal impact on the design of the system.
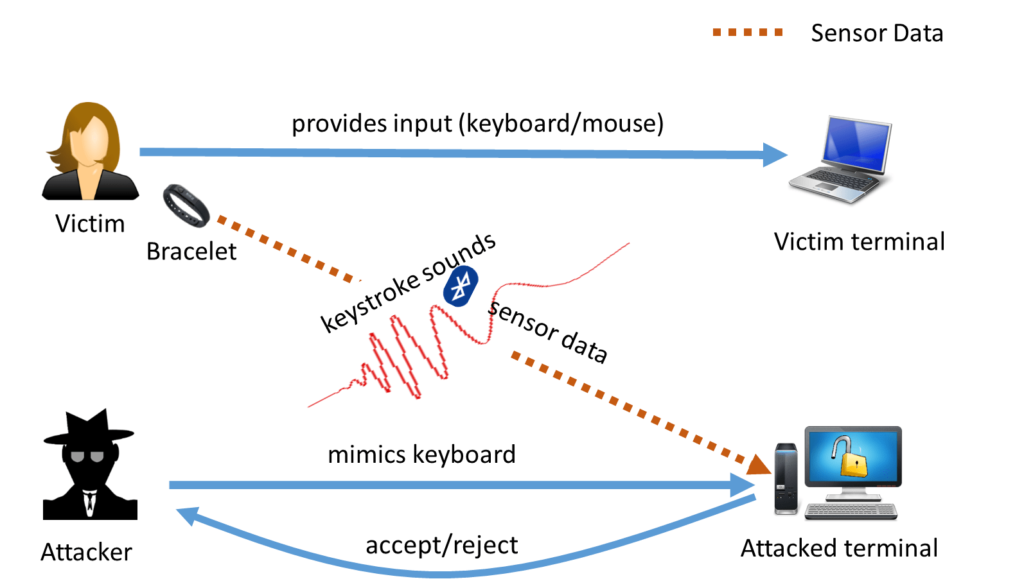
Figure 1: An audio-only opportunistic eavesdropping attack on a zero-effort deauthentication system (e.g. ZEBRA)
We aim to address the sound-based vulnerability of one of the prominent zero-effort deauthentication schemes, called ZEBRA that transparently and continuously authenticates the user using a wearable device wirelessly connected with the authentication terminal. To this end, we designed YELP, a novel and practical defense mechanism based on the principle of sound masking. YELP uses two different types of masking sounds, namely “white noise”, and “music” for cloaking the acoustic side channel leakage underlying the ZEBRA system. We believe that the use of such masking sounds at a reasonable volume level can hide the acoustic leakage emanating from the physical component of the system, and thereby reduce, if not eliminate, the imposed sound-based vulnerability. Indeed, our results show that white noise, as a masking sound, can effectively hide the acoustic leakage from ZEBRA system, thereby significantly reducing the attack success rate of an audio-based side channel attacker while music can moderately hide the acoustic leakage from the system. Our work therefore shows that sound masking can be used as an effective tool in improving the security of (de)authentication systems against an audio-based side channel attack without affecting its original design and without requiring additional effort from the user.
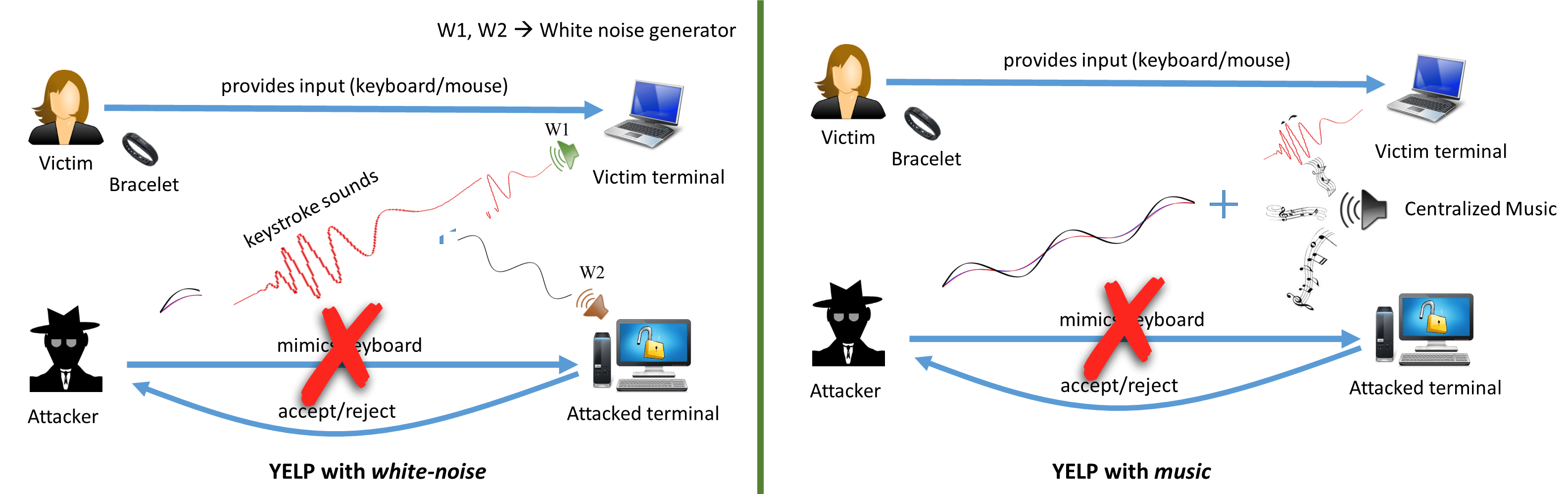
Figure 2: YELP (a sound masking based defense) using a masking signal to thwart an audio only opportunistic eavesdropping attack.
People
Faculty
Student
- Prakash Shrestha (PhD student)
- S Abhishek Anand (PhD candidate)
Publication
- YELP: Masking Sound-based Opportunistic Attacks in Zero-Effort Deauthentication.
Prakash Shrestha, S Abhishek Anand and Nitesh Saxena.
In 10th ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec), 2017.
[pdf]
